Digital Workplace
Today technologies like cloud have made computing a utility and are having a massive impact on the way business activities are undertaken.To be able to make the most of these technologies, you need to transform the way your organization runs its processes and thinks about its business.To be able to do this, new competencies have to be created in the organization to help become more agile, innovative and efficient.
Companies buy and implement tools to achieve digital transformation, but in most organizations the utilization of the tool’s functionality is very limited, in some cases less than 10%.Our offerings are centered around helping customers implement the tools and help them increase the return on the investments that they have made on these tools.
2.1 Office on the Cloud – O365
Office 365 is a productivity suite. Most companies stop after just migrating mail to the cloud.Our services are directed to getting you a higher return on your investment in the Office 365 suite.
We enable adoption of all features of Microsoft O365 – Exchange, SharePoint, Yammer, Skype for Business and Office Pro Plus to deliver outcomes including:
- Planning your roadmap for implementation
- Helping your users learn and use the various products within Office 365
- Identify and sequence the roll out of the various products of the Office 365 suite
- Architect on Sharepoint Online and then integrate existing Sharepoint applications with the applications of SharePoint online
- Planning for backup and DR for your Office 365 environment
- Addressing your technical challenges and pitfalls
- Incorporating office on cloud aligned with enterprise productivity solutions
- Services that provide new agility and capabilities to your business.
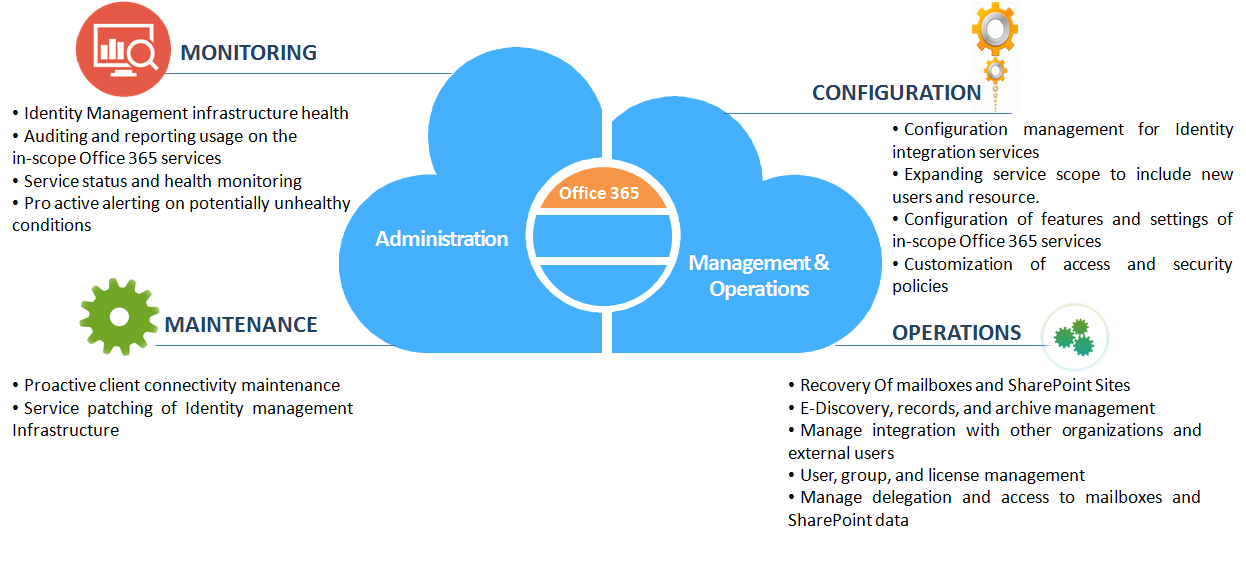
RURIC’s Office 365 services include :
Consulting services
A typical consulting approach includes producing planning documents, project plans, environment assessments and user assessments. Our consultants will engage with your IT teams to assess and build a well thought roadmap aligned with the organizational goals. A technical assessment of the environment will include analysis of services such as email, active directory, SharePoint, collaboration software, file syncing and sharing and more.
Deployment and Migration services
We have expertise and skilled staff to implement an effective end to end Office 365 solution. Migrations from other platform to office 365 typically include all of the data transfer and confirmation of the quality of the data. The overall migration process is dependent on the elements to be migrated and the complexity of the environment. We at RURIC follows proven migration practices to ensure smooth transition without disrupting work.
Ongoing Management services
These services would typically include the ability to set up new user parameters, provide an effective solution for performance degradation, and suggest upgrades or adoption of new versions. The effort is targeted at releasing the client resources while providing management services for the new environment. This includes:
- Service Delivery
- Proactive Services
- Problem Management
- Incident Management
- Change Management
- 24 x 7 Service Availability
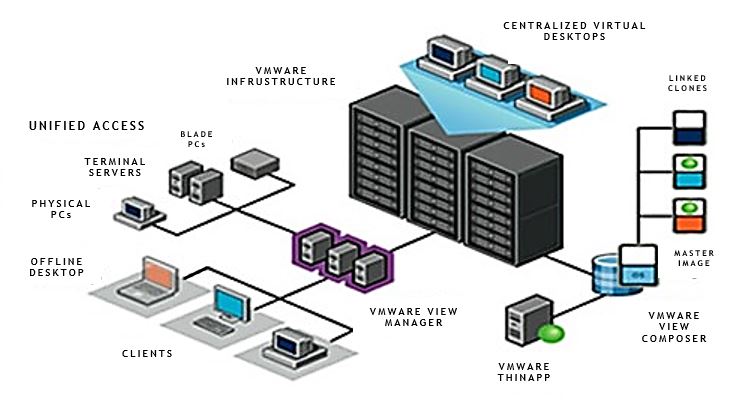
2.2 Desktop Virtualization- VDI
Desktop virtualization can provide a stable operating system environment for users across your company while decreasing overheads. Centrally managed desktop virtualization requires less maintenance and administration by your IT staff and provides greater flexibility to patch, update, or upgrade desktops as needed.
Desktop virtualization infrastructure also lets you extend desktops to the home worker or traveler without compromising your company’s security. Low-power “thin clients” and flat panels can also decrease your office power utilization by as much as 70%. With public IaaS, you can make your journey to VDI a very real possibility.
Desktop virtualization systems work with thin clients, existing Windows, Linux, and Macintosh clients, or over a secure webpage for flexible deployment. And you can centrally manage desktop images for better security and performance:
- Deploy and upgrade applications easily from a central repository.
- Implement secure computing from any endpoint.
- Roll out new desktops and applications in minutes instead of days.
- Reduce energy costs with lower power systems.
We provide complete VDI cloud solutions on:
- IBM® SoftLayer®
- Amazon Web Services (AWS)
- Microsoft® Azure®
2.3 Enterprise App Store
We are all familiar with the concept of “App Store” for the Smart phones, where a set of applications are available and user can download them based on their needs. With the commoditization of IT, users often ask “why can’t we have a similar facility on our Enterprise workstation?
The major benefits of Enterprise App Store are:
- Enhanced User Experience
- Quick Installation of desired application in minutes
- Just couple of clicks required
- Automated Approvals where required
- Automated Software deployment
- Automated check on License Usage
- Optimize Software License Usage
The solution to achieve the above goal of Automated Software Deployment via Enterprise App Store has been built by integrating the following tools and building the workflows:
- Self Service Center from IBM Smart Cloud Control Desk
- Developed Workflow for taking approvals etc
- Developed Scripts to deploy software
- IBM BigFix for software deployment
- IBM Software Use Analysis tool
- Built our solution for integrating the above tools and automating the workflow
2.4 User Experience Monitoring
When you embark on a journey for digital transformation, the user experience is crucial for ensuring the adoption of the productivity solutions. Similarly the performance of customer facing applications determines the popularity of the site and therefore the growth in revenues.
More complex, more distributed and more dynamic than ever before, the modern IT environment needs application performance monitoring and management that matches its agility. Inadequate application performance can directly affect a business, hurting brand image or cutting into revenue as customers struggle to complete transactions.
Application Performance Management (APM) is evolving and growing rapidly, shifting from the legacy of monitoring the network infrastructure to one ensuring the user experience performs well. The increased use of the Web, cloud and mobile applications demand complex products for network engineers and managers to track their performance.
RURIC’s APM services
Our APM solutions help the clients to identify the root cause of delayed/failed transaction and fix them. The application and hosted server are proactively monitored thereby minimizing business impact and help keep clients happy.
We monitor the applications (based on Java, .net and PHP) along with the databases such as Oracle, MYSQL and PostgreSQL and provide code level performance analysis. This granular analysis helps the application developers to fix the specific code/query proactively to ensure flawless application performance. In addition, we:
- Monitor the servers where the applications are hosted for their performance and raise an alert in case of any spike in the system process or the network utilization
- Help reduce L2 and L3 escalations because of the pro active monitoring that we provide.
- Use analytic tools to predict possibilities of failure and take corrective action thereby reducing downtimes
So you get reduced cost and increased productivity.
2.5 Endpoint Security
End points are normally the weakest link in the corporate network. Most of the time the methods to break-in are publicly known vulnerabilities that the end users have not taken steps to prevent.Our services are centered on monitoring end point vulnerabilities and in case of targeted attacks on a given type of systems, we quarantine the systems and curtail the spread of the malware.
Our End Point Management services cover:
- Servers – Patch Management, License Compliance, hardening of systems
- Desktop/Laptops – Patch Management, license compliance, asset management, license usage analysis
- Mobile Devices – Mobile Device Management, Mobile Application Management, Mobile Identity Management, Mobile Content Management
- Vulnerability Assessment and mitigation – Monitoring incidents and events, isolating the threatened systems to stop the spread of an attack and strengthen and reduce the vulnerabilities
- Continuous enforcement of security and regulatory policies with up-to-the minute visibility of compliance status.
- Automatic quarantine actions that isolate out of compliance endpoints until remediation is complete.
- Reduced patching cycles from days or weeks to hours with a 98 per cent first-pass success rate.
Mobile Device Management
Till a few years back, Mobile Device Management used to be different from desktop management.With the advent of the Windows 10 and the recent versions of IOS, the OS on the mobile device, laptop & tablet is similar.Which means the management of the devices gets more streamlined.
This also brings in more complexity to the environment because you could have a policy of BYOD along with company owned devices. To operate in this environment our mobility services ensure secure access to mobile devices, managing the enterprise app store, quarantining a device, wiping it and backing it up.
In addition since there is a whole lot of data which a UEM accumulates, we help you run analytics on it and see trends which can help you reduce your costs and increase productivity.
Closed Loop Security
Generally people look at endpoint security, network security, SIEM in isolation.Our Closed Loop Security services take a holistic view of the security posture of the organization.
We believe that the end-points are the weakest link in the organization’s security posture; we need to monitor it on a continuous basis. Similarly there are a lot of Security incidents/ events which are getting monitored by the SIEM solution that you may have. We look at correlating, analyzing and using analytics on the multiple tools that you use to identify and mitigate risks.
As an example if the SIEM package is throwing up alerts about a specific type of targeted attack on a set of end points, then we isolate and quarantine the end points using the end point management tool.We analyze the SIEM data and identify the vulnerability that the attacker was targeting and look for a remediation. Using the endpoint management tool we patch the endpoints which had the vulnerability. As a next step we then scan all the endpoints to see if the vulnerability exists in any other system and we patch them also.